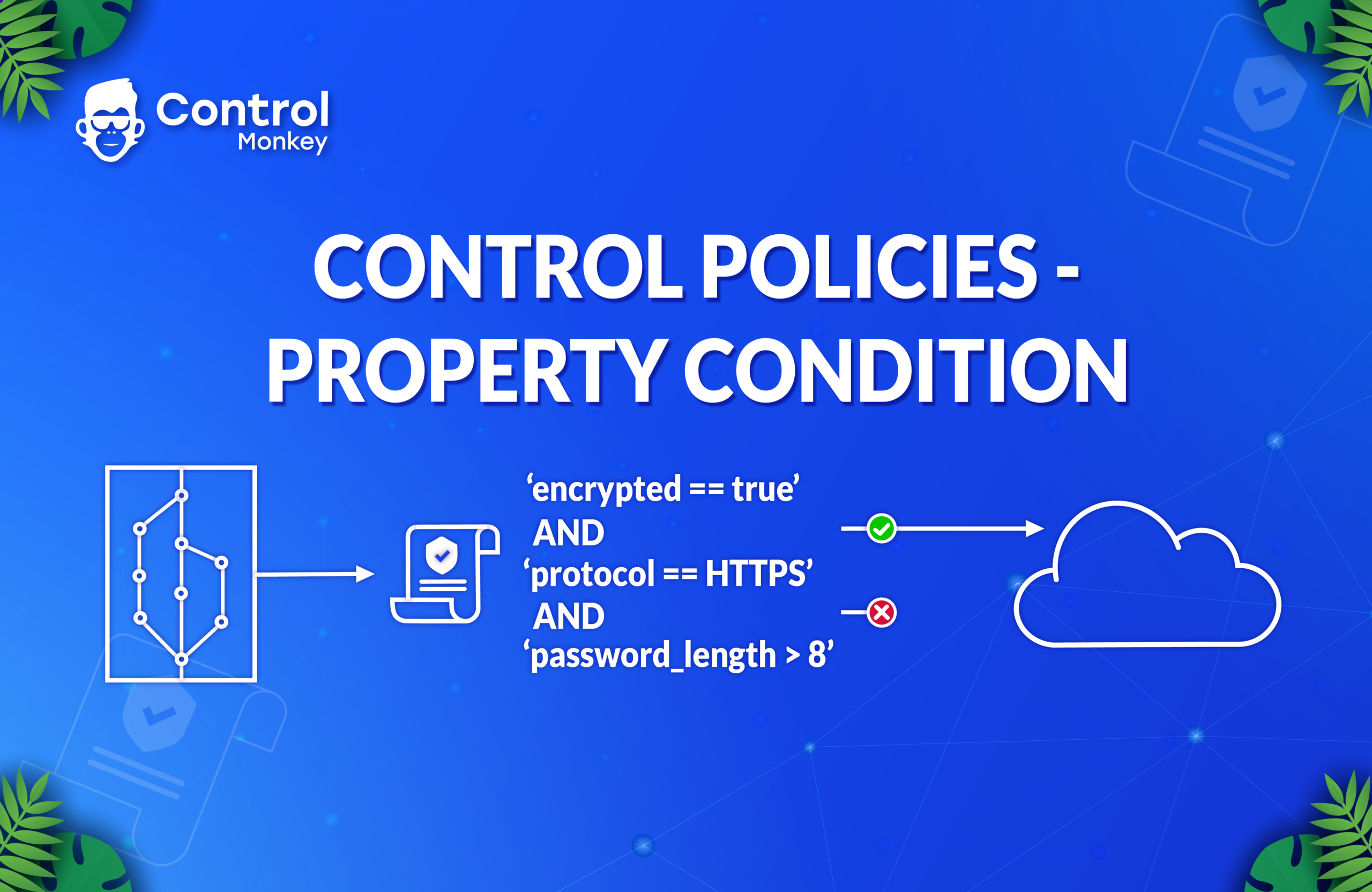
Today ControlMonkey is happy to announce a new Control Policy type – ‘Property Condition’ that enhances our users’ ability to set custom preventive conditions on their cloud resources as part of their Terraform pipeline.
ControlMonkey’s Control Policies serve as preventive controls as part of our GitOps CI/CD Pipeline and help DevOps avoid errors and misconfigurations in production environments.
Leveraging Control Policies is the best practice for enforcing security and compliance in your cloud environment.
Using the new ‘Property Condition’ Control Policy, DevOps teams are now able to set any rule on any resource they wish, without even writing a single line of code (vs other options like writing OPA or Sentinel Code).
For example:
- Denying creating of load balancers without SSL configuration
- Denying creation of EBS volumes with the type of gp2.
- Allowing route 53 record TTL to be less than 60 seconds only.
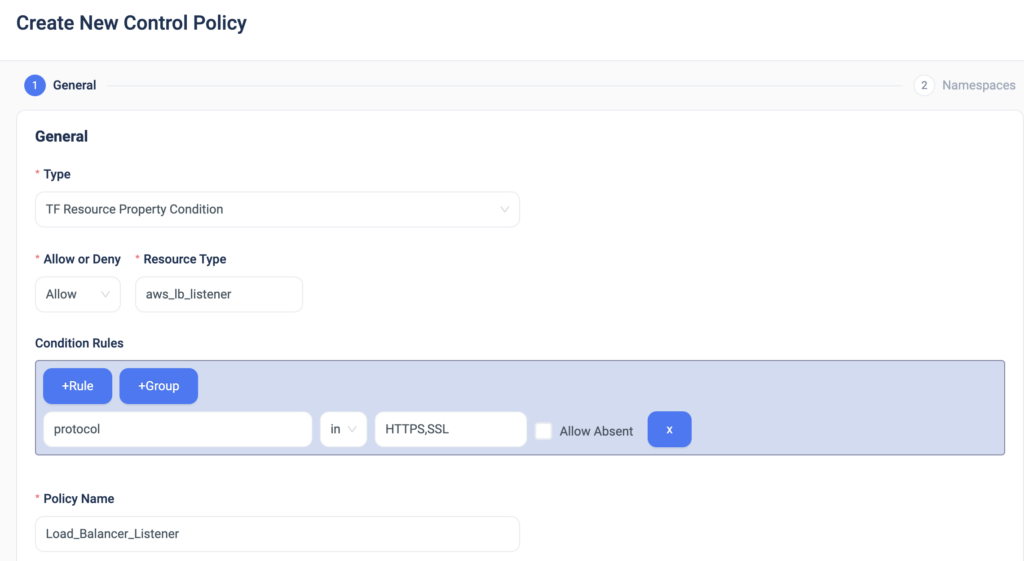


By setting preventive conditions on any cloud resource before it’s being provisioned, DevOps teams gain better control and governance over their cloud environment and overall improve their security and compliance posture.