Intro
When it comes to disaster recovery, most discussions focus on data restoration.
Yet, a critical component often overlooked is the configuration of your cloud infrastructure.
Have you heard about the recent incident in which Google Cloud Platform accidentally deleted an entire customer account?
Events like these underscore the critical need for robust disaster recovery strategies, not just for data but also for cloud infrastructure configurations.
Having DR plans for both data restoration and cloud configuration restoration directly affects your Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO).
I have a question for you.
What happens if a critical piece of your infrastructure is unexpectedly deleted?
Do you have the tools to reproduce it accurately and swiftly?
The Importance of ‘Point-in-Time’ Infrastructure Configurations
Just as diligent database administrators maintain daily backups of critical data, cloud leaders must adopt a similar discipline for infrastructure configurations.
This practice isn’t about reinventing the wheel, but rather, it’s about applying proven methodologies to a new domain to ensure resilience and compliance.
By taking daily snapshots of your infrastructure’s state, you effectively create a “rewind” capability for your configurations.
This allows your organization to restore a previous state quickly and accurately, maintaining an RPO that aligns with your SLAs and upholds your commitments to customers.

Creating a Reliable Baseline with
Infrastructure-as-Code (IaC)
So far, we’ve discussed the what and why—now, let’s talk about the how.
The answer lies in Infrastructure-as-Code (IaC). IaC allows you to “write down” the current configuration of your cloud environment, creating what is essentially a snapshot of your cloud at any given point in time. This baseline is not merely a static record but a dynamic blueprint that can be used to restore your infrastructure to its precise state before any incident.
Let’s consider an example involving your load balancer, complete with its port and redirect configurations. Imagine if someone documented these settings daily using IaC tools like Terraform, OpenTufo, or CloudFormation.
Now, instead of relying on “someone” to document these configurations manually, why not level up and automate the process?
Automating Recovery with Daily Snapshots
To effectively incorporate IaC into your disaster recovery strategy, you need mechanisms in place to generate IaC code from your existing cloud environments. Automating this process to occur daily ensures that your RPO meets a 24-hour window.
Now, where should you store these configuration snapshots? I strongly recommend keeping them in your Git repositories.

By storing these snapshots in your Git repositories, you achieve two significant benefits. First, it simplifies the restoration process. In the event of a disaster, your infrastructure pipeline can directly connect to your Git repository to restore configurations.
Second, it enables meticulous tracking of changes over time, providing a clear audit trail of your infrastructure’s evolution.
Moreover, this setup allows for recovery to a specific commit SHA in your Git repository, mirroring advanced features like Amazon Aurora’s “point-in-time recovery” capability.
Just as AWS allows users to roll back to specific database states with precision, storing IaC snapshots in Git empowers you to revert your infrastructure to any previous configuration documented by a commit, ensuring that you can recover swiftly and accurately to the desired state.
Summary
Having a disaster recovery plan that includes only data backup is no longer sufficient. Infrastructure-as-Code is not just an option; it’s an essential component of a comprehensive disaster recovery strategy.
By integrating IaC, organizations can ensure quicker, more accurate recovery operations, ultimately safeguarding their operational integrity in the face of unexpected disruptions.
About ControlMonkey
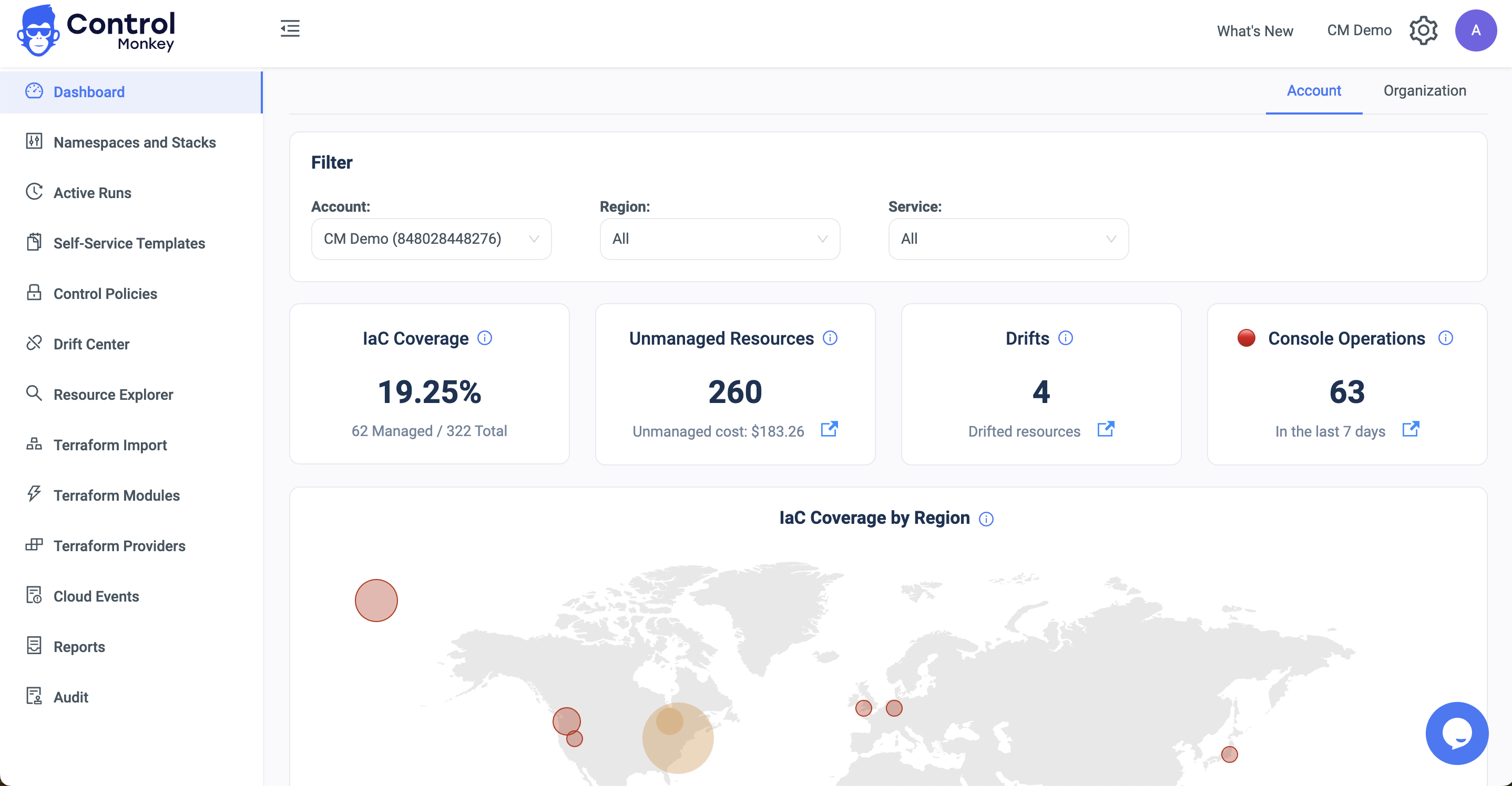
ControlMonkey is the most comprehensive Terraform Automation Platform, providing users with a 360 solution to manage the cloud at scale with Terraform.
You get a single control plane that provides you with a full cloud inventory and helps you understand your IaC Coverage comprehensively. It also offers Terraform code generation for your existing cloud environments, plus drift detection and remediation.
With ControlMonkey, you can standardize your infrastructure delivery at scale with out-of-the-box GitOps Terraform CI/CD, incorporating cost, security, and compliance policies, plus a self-service catalog of pre-defined, compliant infrastructure blueprints for other teams in the organization to spin up infrastructure, enabling agility without sacrificing control.
With ControlMonkey, you can be confident that everything running in your cloud is correctly configured and is supposed to be there.
Book a 1:1 consultation session with our Terraform Experts to learn more about our Terraform Automation platform.